Internet
Wadware: The Silent Threat Lurking in Cyberspace

Welcome to the shadowy realm of cyberspace, where unseen threats lurk in the digital shadows. Among these silent menaces lies a cunning adversary known as Wadware – a stealthy form of malware that can wreak havoc on individuals and businesses alike. In this blog post, we will delve into the world of Wadware, exploring its various types, impacts, and, most importantly, how you can safeguard yourself against its insidious attacks. So buckle up and get ready to navigate the treacherous waters of cybersecurity with us!
Types of Wadware and How They Work
Wadware comes in various forms, each designed to infiltrate systems and wreak havoc. One common type is adware, which bombards users with unwanted advertisements by tracking their online activities. Spyware is another insidious variant that stealthily monitors user behavior, collecting sensitive information without consent.
Keyloggers are a particularly malicious form of wadware that record keystrokes and login credentials, posing a significant threat to personal privacy and security. Another type is ransomware, which encrypts files or locks users out of their devices until a ransom is paid.
Moreover, Trojans disguise themselves as legitimate software to deceive users into downloading them, allowing cybercriminals access to the victim’s system. Rootkits are yet another dangerous form of wadware that can hide deep within the operating system, making detection and removal challenging for even seasoned cybersecurity professionals.
The Impact of Wadware on Individuals and Businesses
Wadware poses a significant threat to both individuals and businesses in the digital realm. For individuals, falling victim to wadware can result in compromised personal information, financial loss, and even identity theft. The invasion of privacy that comes with wadware attacks can be distressing and have long-lasting consequences on one’s sense of security.
On the other hand, for businesses, the impact of wadware can be catastrophic. From confidential data breaches to operational disruptions, wadware attacks can lead to substantial financial losses and damage to reputation. The costs associated with mitigating these attacks and rebuilding trust with customers can be overwhelming for businesses of any size.
In today’s interconnected world, where data is increasingly valuable, safeguarding against wadware is crucial for both individuals and organizations alike. Vigilance in detecting potential threats and implementing robust cybersecurity measures are essential in combating this silent but pervasive danger lurking in cyberspace.
How to Protect Yourself from Wadware Attacks
In the ever-evolving landscape of cybersecurity, protecting yourself from wadware attacks is crucial. Start by ensuring your devices have up-to-date antivirus software and firewalls. Regularly update your operating systems and applications to patch vulnerabilities that wadware can exploit.
Be cautious when clicking on links or downloading attachments from unknown sources, as they could be vehicles for wadware infiltration. Avoid visiting suspicious websites and always verify the legitimacy of emails before interacting with them.
Implement strong passwords and enable two-factor authentication whenever possible to add an extra layer of security. Backup your important data regularly to prevent loss in case of a wadware attack.
Stay informed about the latest cybersecurity threats and trends to stay one step ahead of potential wadware attacks. Remember, vigilance is key when it comes to safeguarding your digital assets from malicious actors lurking in cyberspace.
Case Studies: Real-Life Examples of Wadware Attacks
Imagine a scenario where a small business owner wakes up one morning to find their entire customer database compromised by Wadware. Personal information, credit card details, and sensitive data stolen in the blink of an eye. The aftermath? A reputation tarnished, trust shattered, and financial losses that could cripple the business.
In another case, a cybersecurity firm fell victim to a sophisticated Wad-ware attack targeting their research and development files. Months of hard work and innovation gone in an instant as hackers encrypted crucial data for ransom.
These real-life examples serve as stark reminders of the devastating impact wadware attacks can have on individuals and businesses alike. It’s not just about losing data; it’s about losing trust, credibility, and potentially everything you’ve worked so hard to build. Stay vigilant, stay informed – because in today’s digital landscape, no one is immune to the silent threat of wadware lurking in cyberspace.
The Future of Wadware and Cybersecurity Measures
As technology continues to advance, the future of wadware poses an ongoing threat in cyberspace. With cybercriminals constantly evolving their tactics, it is crucial for individuals and businesses to stay vigilant.
Cybersecurity measures are also adapting to combat these sophisticated attacks. From advanced encryption protocols to robust firewalls, organizations are investing heavily in protecting their digital assets.
Machine learning and artificial intelligence are being integrated into cybersecurity systems to detect and prevent wadware attacks more effectively. By analyzing patterns and anomalies in data traffic, these technologies can proactively defend against threats.
Additionally, cloud-based security solutions offer scalability and flexibility in safeguarding networks from wadware infiltration. As more data migrates to the cloud, ensuring its protection becomes paramount.
Collaboration among industry experts, government agencies, and cybersecurity professionals will be essential in staying ahead of wadware developments. The collective effort towards sharing threat intelligence and best practices will strengthen our defense mechanisms against future cyber threats.
Conclusion
As technology continues to advance, so do the threats in cyberspace. Wadware poses a silent but dangerous risk to individuals and businesses alike. With its ability to evade detection and cause significant harm, it is crucial for everyone to be aware of this threat and take proactive measures to protect themselves.
By understanding the types of wadware attacks and how they work, individuals can better safeguard their devices and personal information. Implementing cybersecurity best practices such as regularly updating software, using strong passwords, and being cautious of suspicious links or downloads can help mitigate the risks associated with wad-ware.
Furthermore, organizations must invest in robust cybersecurity measures to defend against sophisticated wad-ware attacks that could potentially compromise sensitive data and disrupt business operations. Regular security assessments, employee training programs, and implementing multi-layered defense mechanisms are essential steps in fortifying defenses against evolving cyber threats like wad-ware.
In a constantly evolving digital landscape, staying informed about emerging threats like wad-ware is crucial for maintaining a secure online presence. By taking proactive steps to enhance cybersecurity resilience at both individual and organizational levels, we can collectively combat the silent threat lurking in cyberspace – wad–ware.

Internet
241542903: A Blog Article that Will Leave You Questioning Everything

Welcome to a world where reality blurs with the extraordinary, where the lines between what we know and what remains a mystery are tantalizingly thin. Enter the enigmatic realm of 241542903 – a sequence of numbers that holds within it secrets beyond our comprehension. Join us on this mind-bending journey as we delve deep into the mysteries surrounding 241542903, sparking questions that may challenge everything you thought you knew.
The Origin and Meaning of 241542903
Have you ever come across the mysterious number sequence 241542903 and wondered about its significance? The origin of this enigmatic combination remains shrouded in mystery, sparking curiosity and intrigue among those who encounter it. Some believe it holds a deeper meaning beyond just random digits, while others wonder if it’s a cosmic code waiting to be deciphered.
The interpretation of 241542903 varies widely depending on who you ask. For some, it represents a mathematical pattern waiting to be unraveled, while for others, it might symbolize spiritual awakening or synchronicity in the universe. Regardless of how one views it, there’s an undeniable sense of fascination that surrounds this numerical sequence.
As we delve deeper into the origins and meanings behind 241542903, we are confronted with more questions than answers. Could there be hidden messages encoded within these numbers? Or is it simply a coincidence that has captured our attention? Only time will tell as we continue to explore the mysteries surrounding 241542903.
Scientific Explanations and Theories Behind 241542903
Have you ever pondered the mysterious phenomenon of 241542903? Scientists and researchers have delved into this enigmatic sequence, attempting to unravel its meaning. Some believe it could be a cosmic code embedded in the fabric of the universe, while others propose more earthly origins.
One theory suggests that 241542903 may hold a connection to quantum mechanics, with its intricate patterns reflecting fundamental principles of reality. Another perspective considers the possibility of hidden mathematical algorithms governing our existence, with 241542903 serving as a key to unlocking profound truths.
As we explore the scientific explanations behind 241542903, we are confronted with more questions than answers. The complexity and depth of this numerical sequence continue to baffle even the most seasoned experts in various fields. Could there be undiscovered layers of knowledge waiting to be uncovered within 241542903? Only time will tell as we venture further into this intriguing mystery.
Personal Experiences with 241542903
Have you ever experienced the strange phenomenon of 241542903? Many individuals around the world have reported surreal encounters with this mysterious number sequence. Some claim to see it repeatedly in their daily lives, while others stumble upon it in unexpected places.
One person shared how they kept noticing 241542903 on license plates, clocks, and even receipts. Another described feeling a sense of unease whenever confronted with these digits, as if they held some hidden significance waiting to be unraveled.
Interestingly, some believe that encountering 241542903 is a sign from the universe or a message from beyond. Whether coincidence or cosmic alignment, there’s an undeniable intrigue surrounding this enigmatic sequence that continues to captivate those who experience it firsthand.
How 241542903 is Changing Our Perspectives
Have you ever stumbled upon something so mind-boggling that it made you question everything you thought you knew? Enter 241542903. This enigmatic sequence of numbers has been stirring curiosity and challenging conventional beliefs.
As we delve deeper into the mystery surrounding 24154-2903, our perspectives begin to shift. It forces us to reconsider the boundaries of what is possible and challenges us to think beyond the confines of our current knowledge.
The mere mention of 24154-2903 sparks a sense of wonder and intrigue, leading us down paths we never imagined exploring. Its presence is like a catalyst for innovation and open-mindedness, pushing us to expand our horizons and embrace new ideas.
In a world where certainty often reigns supreme, 24154-2903 introduces an element of uncertainty that is both exhilarating and terrifying. It invites us to step outside our comfort zones and confront the unknown with an open mind.
So, as we continue on this journey of discovery alongside 241542903, let’s remember that sometimes it’s in questioning everything that we truly find answers.
The Controversy behind 241542903
The controversy surrounding 241542903 is as enigmatic as the number itself. Some believe it holds the key to unlocking unknown dimensions of reality, while others dismiss it as mere coincidence or superstition.
Critics argue that attributing significance to a seemingly random sequence of numbers is nothing more than human tendency to seek patterns where there are none. Skeptics question the validity of personal experiences shared by those who claim to have encountered 241542903 in their lives.
Despite the skepticism, proponents of 241542903 remain steadfast in their belief that there is something profound and unexplainable about this mysterious number. It continues to spark debates among scientists, spiritualists, and skeptics alike.
As discussions around 241542903 persist, one thing remains clear – its impact on individuals’ beliefs and perspectives cannot be ignored. Whether you view it as a simple numerical coincidence or a gateway to deeper understanding, the controversy surrounding 241542903 invites us all to question our assumptions about the nature of reality.
Conclusion
In this ever-evolving world of mysteries and wonders, the enigmatic concept of 241542903 has sparked curiosity and contemplation among many. Its origin remains shrouded in mystery, with various scientific theories attempting to shed light on its meaning.
Personal experiences shared by individuals have added layers of complexity to our understanding of 241542903. Challenging conventional perspectives and inviting us to question the limits of our knowledge.
As we navigate through the controversy surrounding 24154-2903. One thing is certain – it has undeniably left us questioning everything we thought we knew. Whether a mere numerical sequence or a gateway to new realms of understanding, 241542903 continues to intrigue and captivate minds across the globe.
So, as we ponder the significance of this cryptic code. Let’s embrace the uncertainty it brings and remain open to exploring new possibilities that may lie beyond our current comprehension. After all, in a universe filled with infinite mysteries, perhaps it is in embracing the unknown that we truly find enlightenment.
Internet
Elevate Your Skills with Totk on PC: Strategies for Domination

Welcome to the thrilling world of Totk on PC, where strategic gameplay meets intense action in an epic battle for domination! Whether you’re a seasoned gamer looking to sharpen your skills or a newcomer eager to rise through the ranks, Totk offers an exhilarating experience that will keep you on the edge of your seat. Join us as we delve into the intricacies of this dynamic game, uncovering tips and strategies to help you conquer the competition and reign supreme on the leaderboards. Let’s dive in and elevate your gaming prowess with Totk on PC!
Understanding the basic mechanics and controls
Diving into Totk on PC for the first time can be a thrilling experience, but mastering the basic mechanics and controls is essential to excel in this fast-paced game. Understanding how to move your character seamlessly across the map, aim accurately at opponents, and utilize special abilities effectively are key components that will set you apart from other players.
The WASD keys control movement, while the mouse allows you to aim and shoot. Mastering these fundamental controls is crucial for outmaneuvering enemies in intense battles. Familiarizing yourself with different weapon types and their unique characteristics will give you an edge in combat situations.
Take time to explore each map layout as it can provide strategic advantages such as high ground positions or hidden paths. Practice makes perfect when it comes to mastering the basics of Totk, so don’t hesitate to spend time honing your skills in solo matches before diving into competitive gameplay.
Choosing the right character for your playstyle
When diving into the world of Totk on PC, one crucial decision can shape your gameplay experience – choosing the right character for your playstyle. Each character in Totk comes with unique abilities and attributes that cater to different strategies and preferences.
Before making your selection, take some time to experiment with various characters in practice rounds to understand their strengths and weaknesses. Are you someone who prefers a more aggressive approach? Then a character with high damage output might be ideal for you. Alternatively, if you enjoy supporting your team, look for characters with healing or buffing abilities.
Consider how each character’s skills complement your preferred playstyle. Do you like engaging enemies from a distance or up close? Factor this into your decision-making process as well. Remember, finding the perfect match between character and playstyle can significantly impact your performance on the battlefield.
So, whether you thrive as a frontline tank absorbing damage or excel as a nimble assassin picking off foes swiftly, choose wisely to maximize your effectiveness in Totk!
Tips for effective team coordination and communication
Effective team coordination and communication are essential in Totk to secure victory. To excel in teamwork, establish clear roles and responsibilities for each team member. Assign tasks based on individual strengths to maximize efficiency during gameplay.
Utilize in-game voice chat or messaging systems to communicate with your teammates swiftly. Sharing real-time information about enemy positions or potential strategies can give your team a crucial edge over the competition. Remember, concise and timely communication is key to success.
Implementing a strategy before the match starts can set the tone for effective cooperation throughout the game. Discuss tactics, objectives, and potential challenges with your team beforehand to ensure everyone is on the same page.
Practice active listening skills by being receptive to feedback from your teammates. Adapt and adjust your approach based on their input to optimize teamwork synergy during intense battles.
Mastering different game modes
When it comes to mastering different game modes in Totk on PC, versatility is key. Each mode offers a unique set of challenges and objectives that require adaptability and quick thinking.
Take the time to familiarize yourself with each mode’s specific rules and goals. Whether it’s Capture the Flag, Team Deathmatch, or King of the Hill, understanding the nuances of each will give you a strategic edge.
Experiment with various playstyles and strategies across different game modes. What works well in one mode may not necessarily translate to success in another. Stay flexible and be willing to adjust your approach based on the requirements of each match.
Don’t be afraid to communicate with your team members during gameplay. Coordination and teamwork are essential for achieving victory, especially in objective-based modes where cooperation can make all the difference.
By honing your skills across different game modes, you’ll become a more well-rounded player capable of adapting to any situation that arises in Totk on PC.
Utilizing power-ups and boosts to gain an advantage
Power-ups and boosts can be a game-changer in Totk on PC. These special items provide unique abilities that can give you the upper hand in battles. When used strategically, power-ups can turn the tide of a match in your favor. Keep an eye out for these valuable resources during gameplay, as they can make all the difference between victory and defeat.
Experiment with different power-ups to see which ones align best with your playstyle. Some may enhance your offensive capabilities, while others could boost your defensive skills. Understanding how each power-up works is essential for maximizing their potential impact on the battlefield.
Timing is key when it comes to using power-ups effectively. Save them for critical moments or strategic opportunities where they can have the most significant impact. Coordinate with your team to synchronize power-up usage for maximum efficiency and coordination on the battlefield.
Don’t underestimate the value of power-ups in gaining an advantage over your opponents. Incorporating these tools into your gameplay strategy can elevate your performance and help secure victories in Totk on PC!
Advanced strategies for dominating the competition
Ready to take your Totk skills to the next level? Advanced strategies are key to dominating the competition and securing victory. One effective tactic is mastering map control – understanding the layout and strategically positioning yourself for maximum impact.
Utilize team composition wisely by creating a balanced lineup that covers all essential roles. Coordination with your teammates is crucial; communicate effectively, coordinate attacks, and support each other in battle.
Be adaptable and stay one step ahead of your opponents by anticipating their moves and adjusting your strategy accordingly. Utilize power-ups strategically to gain an edge during critical moments in the game.
Take advantage of boosts such as speed or damage buffs to turn the tide in your favor when needed most. Remember, practice makes perfect, so hone your skills through consistent gameplay and never underestimate the power of continuous improvement.
How to improve your skills and stay on top of the leaderboards
To improve your skills and dominate the leaderboards in Totk on PC, consistent practice is key. Spend time honing your abilities with different characters and mastering their unique powers. Experiment with various strategies to find what works best for you in different game modes.
Watching gameplay videos and studying top players can provide valuable insights into advanced techniques and tactics. Pay attention to their movements, decision-making processes, and team coordination skills to elevate your own gameplay.
Furthermore, don’t underestimate the power of communication in a team-based game like Totk. Clear communication with your teammates can lead to more coordinated attacks and successful defenses against opponents.
Remember that staying on top requires adaptability. Be open to learning from defeats, adjusting your playstyle as needed, and continuously evolving to stay ahead of the competition.
Conclusion
As you embark on your journey to elevate your skills in Totk on PC, remember that practice makes perfect. Utilize the strategies and tips outlined in this guide to dominate the competition and climb the leaderboards. Experiment with different characters, communicate effectively with your team, and master the various game modes to become a formidable player. With dedication and perseverance, you can reach new heights of success in Totk on PC. So gear up, sharpen your skills, and get ready to conquer the virtual battlefield like never before!
Internet
The Science Behind Converting Fahrenheit to Celsius Explained
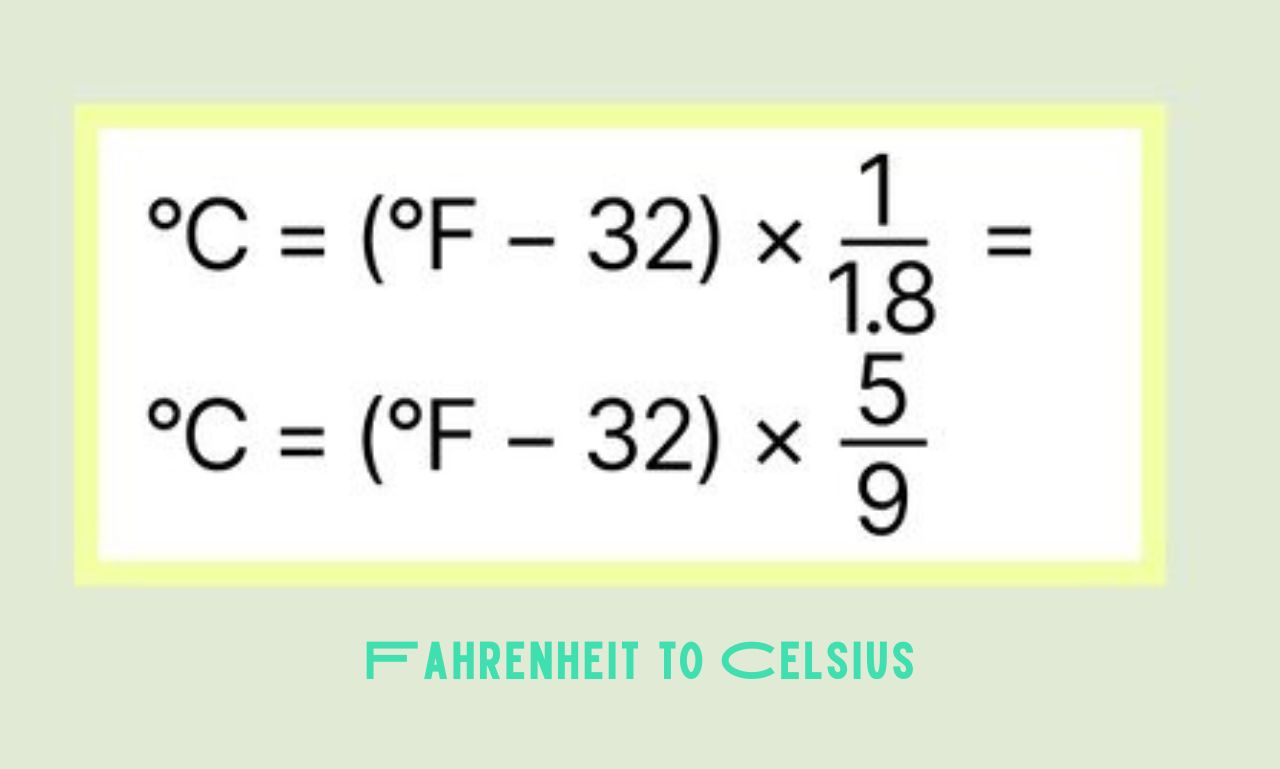
Step into the world of temperature conversion as we unravel the mystery behind Fahrenheit to Celsius! Have you ever wondered how to accurately convert between these two commonly used measurement systems? Join us on a fascinating journey through the science and formulas that make it all possible. Temperature is more than just numbers – it’s a reflection of our environment, our comfort, and our understanding of the world around us. Let’s dive in and explore the captivating realm of Fahrenheit to Celsius conversions together!
What is Fahrenheit and Celsius?
Temperature measurement is a fundamental aspect of our daily lives, impacting everything from weather forecasts to cooking recipes. Two common systems used worldwide are Fahrenheit and Celsius.
Fahrenheit, developed by German physicist Daniel Gabriel Fahrenheit in the early 18th century, sets the freezing point of water at 32 degrees and the boiling point at 212 degrees under standard atmospheric pressure.
Celsius, also known as centigrade, was devised by Swedish astronomer Anders Celsius in the mid-18th century. In this system, water freezes at 0 degrees and boils at 100 degrees under normal atmospheric conditions.
While both scales are widely used globally for measuring temperature, there are differences in their ranges and reference points that make understanding how to convert between them valuable knowledge.
The Formula for Converting Fahrenheit to Celsius
Have you ever wondered about the magic behind converting temperatures from Fahrenheit to Celsius? Well, it’s not as complicated as it may seem. The formula for this conversion is a straightforward mathematical equation that you can easily execute.
To convert Fahrenheit to Celsius, you simply subtract 32 from the Fahrenheit temperature and then multiply the result by 5/9. This simple calculation allows you to accurately determine the equivalent Celsius temperature with precision.
Understanding this formula opens up a world of possibilities when it comes to interpreting temperatures in different units. Whether you’re trying to make sense of weather forecasts or cooking instructions, knowing how to convert between Fahrenheit and Celsius is a valuable skill.
So next time you come across a Fahrenheit temperature reading and need it in Celsius, remember this handy formula – subtract 32, multiply by 5/9, and voila! You’ve successfully converted the temperature unit.
Why Do We Need to Convert Temperatures?
Have you ever wondered why we need to convert temperatures from Fahrenheit to Celsius or vice versa? Well, the answer lies in the global nature of our world. Different countries and industries use different temperature scales, which can lead to confusion if not standardized.
By converting temperatures, we ensure clear communication across borders and disciplines. Whether it’s for international trade, scientific research, or travel purposes, having a universal understanding of temperature measurements is crucial.
Moreover, with advancements in technology and the ease of sharing information globally, accurate conversions are essential. Imagine ordering medication online from a country that uses a different scale – precise temperature conversion ensures you receive the right product.
In essence, converting temperatures isn’t just about numbers; it’s about facilitating efficient communication and ensuring accuracy in various aspects of our interconnected world.
Common Uses of Fahrenheit and Celsius
Both Fahrenheit and Celsius scales are widely used for measuring temperature across the globe. Fahrenheit is commonly used in the United States for weather reports, cooking recipes, and body temperatures. On the other hand, Celsius is more prevalent in scientific research, international communication, and everyday use in most countries.
In daily life, you might see Fahrenheit on your oven or thermostat settings if you’re based in the US. Meanwhile, when traveling internationally or reading scientific literature, you’re likely to encounter Celsius measurements. Understanding both systems can be beneficial depending on your location and field of work.
Whether you’re trying a new recipe that lists temperatures in Fahrenheit or discussing global warming trends using Celsius data points – knowing how to convert between these two temperature scales can be a handy skill to have!
Tips for Accurate Conversions
- When it comes to converting temperatures from Fahrenheit to Celsius, accuracy is key. Here are some tips to ensure you get the right conversion every time.
- Always double-check the formula you’re using. It’s easy to mix up formulas or make calculation errors, so take your time and avoid rushing through the process.
- Round numbers appropriately. While conversions may result in decimals, rounding them off can help simplify the final temperature for practical use.
- Be mindful of negative numbers when converting between Fahrenheit and Celsius. Remember that negative temperatures behave differently on each scale.
- Consider using online conversion tools or apps for quick and accurate results. These resources can save time and eliminate manual calculation errors.
Conclusion:
Understanding the science behind converting Fahrenheit to Celsius empowers us to navigate temperature measurements with ease. By grasping the formulas and reasons for conversion, we can seamlessly switch between these two common scales. Whether you’re preparing a recipe, checking the weather forecast, or working in scientific research, knowing how to convert temperatures accurately is a valuable skill. With practice and the tips provided, you can confidently handle conversions between Fahrenheit and Celsius like a pro. Embrace the knowledge of temperature measurement systems and elevate your proficiency in dealing with varying climates and environments.
-

 Business2 months ago
Business2 months agoWhat does Incumbent mean in business?
-

 Text2 months ago
Text2 months agoPH
-

 Text2 months ago
Text2 months agoWhat does smh mean in text?
-

 Text2 months ago
Text2 months agoKN
-

 News1 month ago
News1 month agoDiscover MyLawyer360: Your One-Stop Legal Assistance Hub
-

 Business1 month ago
Business1 month agoLessInvest.com Crypto: Your Gateway to Smarter Investments
-

 sports1 month ago
sports1 month agoThe Versatile Talent of ben foster: A Deep Dive into His Career
-

 Health1 month ago
Health1 month agoThe Comprehensive Guide to Mega-Personal.net Health Archives