Internet
Maximizecache.shop: Your Go-To Source for Quality Cache Solutions

Looking to turbocharge your website’s performance and boost user experience? Look no further than Maximizecache.shop! With a wide range of cutting-edge cache solutions, this online hub is your one-stop shop for all things caching. Say goodbye to slow loading times and hello to seamless browsing with Maximizecache.shop by your side. Let’s dive into the world of cache solutions together!
The Importance of Cache Solutions
In today’s fast-paced digital world, the importance of cache solutions cannot be overstated. Cache plays a vital role in enhancing website performance and user experience by storing frequently accessed data closer to the end-user.
By utilizing cache solutions, websites can load faster, leading to lower bounce rates and increased visitor engagement. This is crucial for businesses looking to stay competitive and retain their online audience.
Cache solutions also help reduce server load by serving cached content instead of repeatedly fetching it from the webserver. This not only improves website speed but also contributes to cost savings on server resources.
Moreover, caching can improve search engine rankings as faster-loading websites are favored by search algorithms. This means that implementing effective cache solutions can have a direct impact on your website’s visibility and organic traffic growth.
Investing in high-quality cache solutions like those offered by Maximizecache.shop is essential for any business looking to optimize its online presence and deliver an exceptional user experience.
Types of Cache Offered by Maximizecache.shop
Maximizecache.shop offers a variety of cache solutions to meet different business needs. One type of cache they offer is server-side caching, which helps speed up website loading times by storing frequently accessed data. This can significantly improve user experience and SEO rankings by reducing page load times.
Another type of cache provided by Maximizecache.shop is browser caching. By storing static files like images and CSS on users’ devices temporarily, websites can load faster upon revisits, enhancing overall performance. This feature is crucial for retaining visitors who expect quick and seamless browsing experiences.
Additionally, Maximizecache.shop offers database caching services to optimize data retrieval processes. By storing query results in memory or disk storage, businesses can reduce the workload on their servers and improve overall database performance.
The diverse range of cache solutions offered by Maximizecache.shop caters to various aspects of website optimization and performance enhancement.
Benefits of Using Maximizecache.shop
When it comes to optimizing your website’s performance, using Maximizecache.shop can provide a range of benefits. One key advantage is the increased speed and efficiency of your site due to the cache solutions offered. This means that visitors will experience quicker loading times and a smoother browsing experience.
Another benefit is improved SEO rankings, as faster websites tend to rank higher in search engine results. By utilizing cache solutions from Maximizecache.shop, you can enhance your online visibility and attract more organic traffic to your site.
Moreover, by reducing server load through caching, you can also save on hosting costs and improve overall website stability. This not only benefits your business financially but also ensures a reliable online presence for your customers.
Choosing Maximizecache.shop for your caching needs can result in enhanced user experience, better search engine visibility, cost savings, and increased website reliability – all factors that contribute to the success of your online venture.
Customer Reviews and Testimonials
Customer reviews and testimonials are like a window into the experience of others who have used Maximizecache.shop. Reading feedback from real customers can provide valuable insights into the quality of service and products offered.
Many satisfied customers praise the efficiency and reliability of Maximizecache.shop’s cache solutions, highlighting how it has improved their online performance significantly. These positive testimonials serve as social proof, instilling trust in potential new customers.
Hearing firsthand accounts from others who have benefited from using Maximizecache.shop can help you make an informed decision about incorporating cache solutions into your business strategy. Don’t just take our word for it – listen to what our happy clients have to say!
How to Use Maximizecache.shop for Your Business Needs
When it comes to using Maximizecache.shop for your business needs, the process is simple and straightforward. Begin by exploring the range of cache solutions offered on the website. Whether you need file caching, object caching, or opcode caching, Maximizecache.shop has got you covered.
Once you’ve identified the type of cache that suits your requirements best, proceed to select the appropriate package based on your business size and traffic volume. The website provides detailed information about each package’s features and benefits to help you make an informed decision.
After selecting a package, complete the easy checkout process to start enjoying improved website performance and speed. The team at Maximizecache.shop is available to provide support and assistance should you encounter any issues during installation or configuration.
By utilizing Maximizecache.shop for your business needs, you can optimize your website’s performance efficiently and effectively. So why wait? Enhance your online presence today with top-notch cache solutions from Maximizecache.shop!
Conclusion: Why Choose Maximizecache.shop?
Maximizecache.shop is your ultimate destination for top-notch cache solutions. With a wide range of cache options to choose from and a track record of satisfied customers, Maximizecache.shop stands out as a reliable source for all your caching needs.
Whether you are looking to boost the performance of your website or improve loading speeds, Maximizecache.shop has you covered with their variety of cache offerings. From browser caching to object caching, they provide comprehensive solutions tailored to meet your specific requirements.
By choosing Maximizecache.shop, you can benefit from enhanced site speed, improved user experience, and increased efficiency. Their easy-to-use platform makes it simple to implement caching strategies that will take your online presence to the next level.
Don’t just take our word for it – explore the testimonials and reviews from satisfied customers who have experienced the difference that Maximizecache.shop can make. Join them in maximizing your caching potential today!
When it comes to quality cache solutions, Maximizecache.shop is undoubtedly the go-to choice for businesses seeking optimal performance and reliability. Elevate your online presence with Maximizecache.shop and unlock a world of possibilities for success in the digital realm.

Internet
Elevate Your Skills with Totk on PC: Strategies for Domination

Welcome to the thrilling world of Totk on PC, where strategic gameplay meets intense action in an epic battle for domination! Whether you’re a seasoned gamer looking to sharpen your skills or a newcomer eager to rise through the ranks, Totk offers an exhilarating experience that will keep you on the edge of your seat. Join us as we delve into the intricacies of this dynamic game, uncovering tips and strategies to help you conquer the competition and reign supreme on the leaderboards. Let’s dive in and elevate your gaming prowess with Totk on PC!
Understanding the basic mechanics and controls
Diving into Totk on PC for the first time can be a thrilling experience, but mastering the basic mechanics and controls is essential to excel in this fast-paced game. Understanding how to move your character seamlessly across the map, aim accurately at opponents, and utilize special abilities effectively are key components that will set you apart from other players.
The WASD keys control movement, while the mouse allows you to aim and shoot. Mastering these fundamental controls is crucial for outmaneuvering enemies in intense battles. Familiarizing yourself with different weapon types and their unique characteristics will give you an edge in combat situations.
Take time to explore each map layout as it can provide strategic advantages such as high ground positions or hidden paths. Practice makes perfect when it comes to mastering the basics of Totk, so don’t hesitate to spend time honing your skills in solo matches before diving into competitive gameplay.
Choosing the right character for your playstyle
When diving into the world of Totk on PC, one crucial decision can shape your gameplay experience – choosing the right character for your playstyle. Each character in Totk comes with unique abilities and attributes that cater to different strategies and preferences.
Before making your selection, take some time to experiment with various characters in practice rounds to understand their strengths and weaknesses. Are you someone who prefers a more aggressive approach? Then a character with high damage output might be ideal for you. Alternatively, if you enjoy supporting your team, look for characters with healing or buffing abilities.
Consider how each character’s skills complement your preferred playstyle. Do you like engaging enemies from a distance or up close? Factor this into your decision-making process as well. Remember, finding the perfect match between character and playstyle can significantly impact your performance on the battlefield.
So, whether you thrive as a frontline tank absorbing damage or excel as a nimble assassin picking off foes swiftly, choose wisely to maximize your effectiveness in Totk!
Tips for effective team coordination and communication
Effective team coordination and communication are essential in Totk to secure victory. To excel in teamwork, establish clear roles and responsibilities for each team member. Assign tasks based on individual strengths to maximize efficiency during gameplay.
Utilize in-game voice chat or messaging systems to communicate with your teammates swiftly. Sharing real-time information about enemy positions or potential strategies can give your team a crucial edge over the competition. Remember, concise and timely communication is key to success.
Implementing a strategy before the match starts can set the tone for effective cooperation throughout the game. Discuss tactics, objectives, and potential challenges with your team beforehand to ensure everyone is on the same page.
Practice active listening skills by being receptive to feedback from your teammates. Adapt and adjust your approach based on their input to optimize teamwork synergy during intense battles.
Mastering different game modes
When it comes to mastering different game modes in Totk on PC, versatility is key. Each mode offers a unique set of challenges and objectives that require adaptability and quick thinking.
Take the time to familiarize yourself with each mode’s specific rules and goals. Whether it’s Capture the Flag, Team Deathmatch, or King of the Hill, understanding the nuances of each will give you a strategic edge.
Experiment with various playstyles and strategies across different game modes. What works well in one mode may not necessarily translate to success in another. Stay flexible and be willing to adjust your approach based on the requirements of each match.
Don’t be afraid to communicate with your team members during gameplay. Coordination and teamwork are essential for achieving victory, especially in objective-based modes where cooperation can make all the difference.
By honing your skills across different game modes, you’ll become a more well-rounded player capable of adapting to any situation that arises in Totk on PC.
Utilizing power-ups and boosts to gain an advantage
Power-ups and boosts can be a game-changer in Totk on PC. These special items provide unique abilities that can give you the upper hand in battles. When used strategically, power-ups can turn the tide of a match in your favor. Keep an eye out for these valuable resources during gameplay, as they can make all the difference between victory and defeat.
Experiment with different power-ups to see which ones align best with your playstyle. Some may enhance your offensive capabilities, while others could boost your defensive skills. Understanding how each power-up works is essential for maximizing their potential impact on the battlefield.
Timing is key when it comes to using power-ups effectively. Save them for critical moments or strategic opportunities where they can have the most significant impact. Coordinate with your team to synchronize power-up usage for maximum efficiency and coordination on the battlefield.
Don’t underestimate the value of power-ups in gaining an advantage over your opponents. Incorporating these tools into your gameplay strategy can elevate your performance and help secure victories in Totk on PC!
Advanced strategies for dominating the competition
Ready to take your Totk skills to the next level? Advanced strategies are key to dominating the competition and securing victory. One effective tactic is mastering map control – understanding the layout and strategically positioning yourself for maximum impact.
Utilize team composition wisely by creating a balanced lineup that covers all essential roles. Coordination with your teammates is crucial; communicate effectively, coordinate attacks, and support each other in battle.
Be adaptable and stay one step ahead of your opponents by anticipating their moves and adjusting your strategy accordingly. Utilize power-ups strategically to gain an edge during critical moments in the game.
Take advantage of boosts such as speed or damage buffs to turn the tide in your favor when needed most. Remember, practice makes perfect, so hone your skills through consistent gameplay and never underestimate the power of continuous improvement.
How to improve your skills and stay on top of the leaderboards
To improve your skills and dominate the leaderboards in Totk on PC, consistent practice is key. Spend time honing your abilities with different characters and mastering their unique powers. Experiment with various strategies to find what works best for you in different game modes.
Watching gameplay videos and studying top players can provide valuable insights into advanced techniques and tactics. Pay attention to their movements, decision-making processes, and team coordination skills to elevate your own gameplay.
Furthermore, don’t underestimate the power of communication in a team-based game like Totk. Clear communication with your teammates can lead to more coordinated attacks and successful defenses against opponents.
Remember that staying on top requires adaptability. Be open to learning from defeats, adjusting your playstyle as needed, and continuously evolving to stay ahead of the competition.
Conclusion
As you embark on your journey to elevate your skills in Totk on PC, remember that practice makes perfect. Utilize the strategies and tips outlined in this guide to dominate the competition and climb the leaderboards. Experiment with different characters, communicate effectively with your team, and master the various game modes to become a formidable player. With dedication and perseverance, you can reach new heights of success in Totk on PC. So gear up, sharpen your skills, and get ready to conquer the virtual battlefield like never before!
Internet
The Science Behind Converting Fahrenheit to Celsius Explained
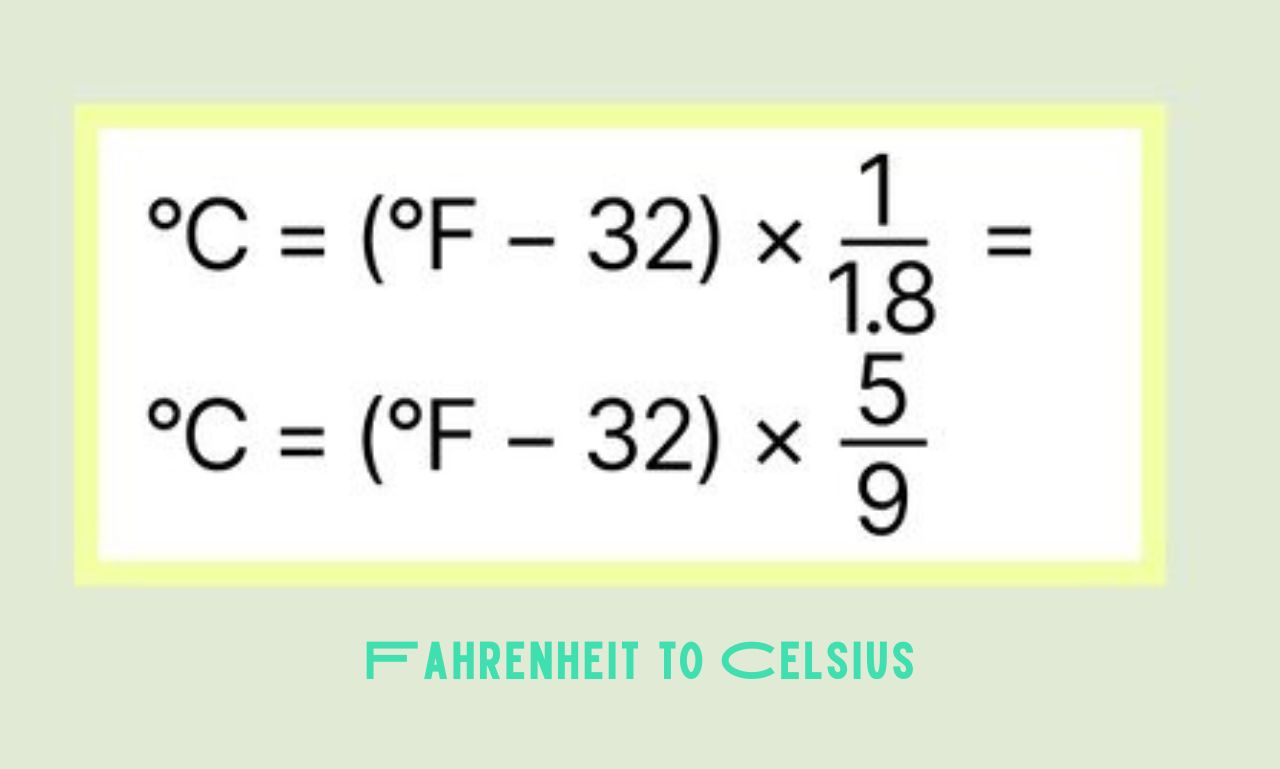
Step into the world of temperature conversion as we unravel the mystery behind Fahrenheit to Celsius! Have you ever wondered how to accurately convert between these two commonly used measurement systems? Join us on a fascinating journey through the science and formulas that make it all possible. Temperature is more than just numbers – it’s a reflection of our environment, our comfort, and our understanding of the world around us. Let’s dive in and explore the captivating realm of Fahrenheit to Celsius conversions together!
What is Fahrenheit and Celsius?
Temperature measurement is a fundamental aspect of our daily lives, impacting everything from weather forecasts to cooking recipes. Two common systems used worldwide are Fahrenheit and Celsius.
Fahrenheit, developed by German physicist Daniel Gabriel Fahrenheit in the early 18th century, sets the freezing point of water at 32 degrees and the boiling point at 212 degrees under standard atmospheric pressure.
Celsius, also known as centigrade, was devised by Swedish astronomer Anders Celsius in the mid-18th century. In this system, water freezes at 0 degrees and boils at 100 degrees under normal atmospheric conditions.
While both scales are widely used globally for measuring temperature, there are differences in their ranges and reference points that make understanding how to convert between them valuable knowledge.
The Formula for Converting Fahrenheit to Celsius
Have you ever wondered about the magic behind converting temperatures from Fahrenheit to Celsius? Well, it’s not as complicated as it may seem. The formula for this conversion is a straightforward mathematical equation that you can easily execute.
To convert Fahrenheit to Celsius, you simply subtract 32 from the Fahrenheit temperature and then multiply the result by 5/9. This simple calculation allows you to accurately determine the equivalent Celsius temperature with precision.
Understanding this formula opens up a world of possibilities when it comes to interpreting temperatures in different units. Whether you’re trying to make sense of weather forecasts or cooking instructions, knowing how to convert between Fahrenheit and Celsius is a valuable skill.
So next time you come across a Fahrenheit temperature reading and need it in Celsius, remember this handy formula – subtract 32, multiply by 5/9, and voila! You’ve successfully converted the temperature unit.
Why Do We Need to Convert Temperatures?
Have you ever wondered why we need to convert temperatures from Fahrenheit to Celsius or vice versa? Well, the answer lies in the global nature of our world. Different countries and industries use different temperature scales, which can lead to confusion if not standardized.
By converting temperatures, we ensure clear communication across borders and disciplines. Whether it’s for international trade, scientific research, or travel purposes, having a universal understanding of temperature measurements is crucial.
Moreover, with advancements in technology and the ease of sharing information globally, accurate conversions are essential. Imagine ordering medication online from a country that uses a different scale – precise temperature conversion ensures you receive the right product.
In essence, converting temperatures isn’t just about numbers; it’s about facilitating efficient communication and ensuring accuracy in various aspects of our interconnected world.
Common Uses of Fahrenheit and Celsius
Both Fahrenheit and Celsius scales are widely used for measuring temperature across the globe. Fahrenheit is commonly used in the United States for weather reports, cooking recipes, and body temperatures. On the other hand, Celsius is more prevalent in scientific research, international communication, and everyday use in most countries.
In daily life, you might see Fahrenheit on your oven or thermostat settings if you’re based in the US. Meanwhile, when traveling internationally or reading scientific literature, you’re likely to encounter Celsius measurements. Understanding both systems can be beneficial depending on your location and field of work.
Whether you’re trying a new recipe that lists temperatures in Fahrenheit or discussing global warming trends using Celsius data points – knowing how to convert between these two temperature scales can be a handy skill to have!
Tips for Accurate Conversions
- When it comes to converting temperatures from Fahrenheit to Celsius, accuracy is key. Here are some tips to ensure you get the right conversion every time.
- Always double-check the formula you’re using. It’s easy to mix up formulas or make calculation errors, so take your time and avoid rushing through the process.
- Round numbers appropriately. While conversions may result in decimals, rounding them off can help simplify the final temperature for practical use.
- Be mindful of negative numbers when converting between Fahrenheit and Celsius. Remember that negative temperatures behave differently on each scale.
- Consider using online conversion tools or apps for quick and accurate results. These resources can save time and eliminate manual calculation errors.
Conclusion:
Understanding the science behind converting Fahrenheit to Celsius empowers us to navigate temperature measurements with ease. By grasping the formulas and reasons for conversion, we can seamlessly switch between these two common scales. Whether you’re preparing a recipe, checking the weather forecast, or working in scientific research, knowing how to convert temperatures accurately is a valuable skill. With practice and the tips provided, you can confidently handle conversions between Fahrenheit and Celsius like a pro. Embrace the knowledge of temperature measurement systems and elevate your proficiency in dealing with varying climates and environments.
Internet
Why SSIS 816 is a Game-Changer for Data Integration: Exploring its Benefits

Are you ready to revolutionize your data integration game? Enter SSIS 816 – the latest powerhouse in the world of data management. In this blog post, we will delve into why SSIS-816 is a complete game-changer and explore how it can transform the way you handle your data processes. So buckle up, because things are about to get exciting!
The History of Data Integration
Data integration has come a long way since the early days of manual data entry and siloed systems. In the past, organizations struggled to connect disparate data sources, leading to inefficiencies and inaccuracies in decision-making. As technology evolved, so did the need for more advanced solutions to streamline data processes.
The evolution of data integration can be traced back to the emergence of ETL (extract, transform, load) tools that automated the process of extracting data from various sources and loading it into a centralized repository. These tools marked a significant shift towards more efficient and scalable data management practices.
With advancements in cloud computing and big data analytics, modern-day data integration platforms like SSIS have revolutionized how businesses handle their information assets. By providing robust capabilities for cleansing, transforming, and integrating large volumes of diverse data sources seamlessly, these tools empower organizations to make better-informed decisions faster than ever before.
Understanding the history of data integration helps us appreciate how far we’ve come in harnessing the power of technology to drive business success through enhanced data management practices.
What Makes SSIS 816 Stand Out?
SSIS 816 is a game-changer in the realm of data integration, setting itself apart with its advanced capabilities and innovative features. What makes SSIS stand out from its predecessors is its enhanced performance and efficiency in handling complex data workflows.
One key aspect that sets SSIS 816 apart is its improved connectivity options, allowing seamless integration with various data sources and systems. Additionally, the enhanced security features ensure that sensitive information remains protected throughout the integration process.
Moreover, SSIS 816 offers a user-friendly interface with an intuitive design, making it easier for users to create and manage data integration tasks efficiently. The ability to automate repetitive tasks further streamlines processes, saving time and resources for organizations.
The combination of speed, flexibility, and ease of use makes SSIS a top choice for businesses looking to optimize their data integration efforts seamlessly.
Key Features and Benefits of SSIS 816
SSIS 816 comes packed with a plethora of key features that set it apart in the world of data integration. One standout feature is its enhanced connectivity options, allowing seamless integration with various data sources and destinations. This flexibility enables users to work across different platforms without constraints.
Another significant benefit of SSIS is its improved performance capabilities. With optimized processing speeds and resource utilization, tasks can be executed faster and more efficiently than ever before. This means less waiting time and increased productivity for users handling large datasets.
Moreover, the intuitive user interface of SSIS makes it easy for both beginners and advanced users to navigate through complex data integration workflows effortlessly. The drag-and-drop functionality simplifies the process of designing packages, reducing the learning curve for new users while offering advanced customization options for experienced professionals.
In addition, SSIS 816 offers robust security features to safeguard sensitive information during data transfers, ensuring compliance with regulations and protecting against potential threats. These comprehensive security measures give users peace of mind when handling confidential data within their organization.
Real-Life Examples of How SSIS 816 Has Improved Data Integration
Imagine a large retail company struggling to consolidate sales data from multiple stores across different regions. With SSIS 816, they seamlessly automated the extraction and transformation process, saving hours of manual work and reducing errors significantly.
In another scenario, a healthcare organization utilized SSIS 816 to streamline patient data integration from various sources. This led to enhanced operational efficiency, improved decision-making processes, and ultimately better patient care outcomes.
Furthermore, a financial institution leveraged SSIS 816 to merge complex datasets for risk analysis. The result? Quicker access to critical information, enabling them to make informed decisions promptly in the fast-paced market environment.
These real-life examples demonstrate how SSIS 816 revolutionizes data integration across diverse industries by simplifying processes and enhancing overall productivity.
Challenges and Limitations of SSIS-816
While SSIS 816 offers a range of benefits for data integration, it does come with its own set of challenges and limitations that users should be aware of. One challenge is the learning curve associated with mastering all the features and functionalities that 816 offers. It may require dedicated time and effort to fully understand how to leverage its capabilities effectively.
Another limitation is the potential complexity of setting up and configuring SSIS-816 for specific data integration tasks. Users may encounter difficulties in properly configuring connections, transformations, and workflows within the tool, especially when dealing with large volumes of data or intricate data structures.
Additionally, as with any software solution, there may be occasional bugs or glitches that could impact the performance or reliability of SSIS-816. It’s important for users to stay updated on patches and fixes released by Microsoft to address any issues that arise during implementation and usage.
Conclusion
SSIS 816 is indeed a game-changer in the world of data integration. With its advanced features and capabilities, it has revolutionized how businesses handle their data processes. The history of data integration has been marked by constant evolution and innovation. SSIS 816 builds upon this legacy by offering cutting-edge solutions for seamless data management.
What makes SSIS 816 stand out is its ability to streamline complex data workflows with ease. Its user-friendly interface empowers organizations to efficiently integrate, transform, and load their data at scale. Key features like enhanced performance, improved connectivity options, and robust security measures make SSIS 816 a top choice for businesses looking to optimize their data integration processes.
Real-life examples showcase how SSIS has transformed organizations by enabling them to make informed decisions based on accurate and timely data insights. While SSIS offers numerous benefits, it also comes with its set of challenges and limitations that organizations need to navigate effectively to maximize its potential.
-

 Business2 months ago
Business2 months agoWhat does Incumbent mean in business?
-

 Text2 months ago
Text2 months agoPH
-

 Text2 months ago
Text2 months agoWhat does smh mean in text?
-

 Text2 months ago
Text2 months agoKN
-

 News1 month ago
News1 month agoDiscover MyLawyer360: Your One-Stop Legal Assistance Hub
-

 Business1 month ago
Business1 month agoLessInvest.com Crypto: Your Gateway to Smarter Investments
-

 sports1 month ago
sports1 month agoThe Versatile Talent of ben foster: A Deep Dive into His Career
-

 Health1 month ago
Health1 month agoThe Comprehensive Guide to Mega-Personal.net Health Archives