Internet
How to Effectively Use the G5335QT2U Datasheet PDF in Your Projects
Are you ready to unlock the full potential of the G5335QT2U in your projects? Dive into this comprehensive guide to discover how to navigate and utilize the G5335QT2U Datasheet PDF like a pro. Whether you’re a seasoned engineer or a curious DIY enthusiast, understanding this datasheet is key to harnessing the power of this versatile component. Let’s delve into decoding its specifications, troubleshooting common issues, exploring practical applications, and uncovering tips for optimal performance. Get ready to take your projects to new heights with the G5335QT2U!
Understanding the G5335QT2U Datasheet PDF
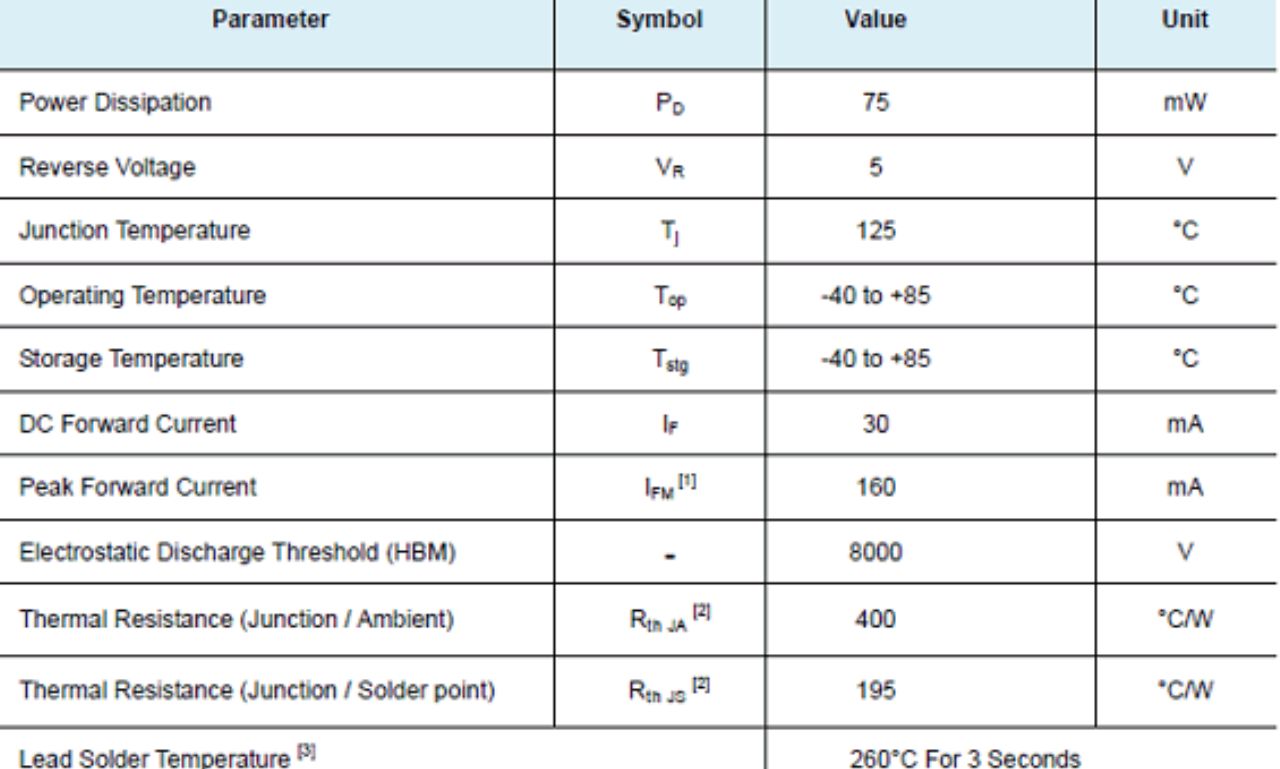
When diving into the G5335QT2U Datasheet PDF, it’s like unraveling a blueprint for your project. This document holds the key to unlocking the potential of this component by providing intricate details and specifications. The datasheet acts as a roadmap, guiding you through the technical aspects and features of the G5335QT2U with precision.
Each section of the datasheet offers valuable insights into different components and parameters, such as voltage ratings, power consumption, input/output configurations, and more. Understanding these details is crucial in selecting and integrating the G5335QT2U effectively into your design.
By studying the datasheet thoroughly, you can gain a deeper understanding of how this component operates within your system. It serves as a reference point for troubleshooting issues that may arise during implementation or testing phases.
Components and Specifications of the G5335QT2U
When working on a project that requires precision and reliability, understanding the components and specifications of the G5335QT2U is crucial. This multifunctional device boasts an array of features designed to enhance performance and efficiency.
The G5335QT2U comes equipped with advanced circuitry that ensures seamless integration into various applications. Its high-quality materials guarantee durability and longevity, even in demanding environments.
With impressive specifications such as voltage ratings, current limits, and frequency ranges clearly outlined in the datasheet PDF, users can tailor their projects to meet specific requirements with ease. The detailed information provided allows for precise planning and execution, resulting in optimal outcomes.
Whether you’re a seasoned professional or a hobbyist tinkering with electronics, having a deep understanding of the components and specifications of the G5335QT2U empowers you to take your projects to new heights.
How to Interpret the Datasheet for Your Specific Project
When diving into a datasheet for the G5335QT2U, it’s crucial to understand its layout and content. The first step is to familiarize yourself with the key components and specifications listed. Pay attention to details like voltage ratings, pin configurations, and operating temperature ranges.
Next, look at the electrical characteristics section to grasp how the device performs under different conditions. This will help you determine if the G5335QT2U is suitable for your specific project requirements.
Don’t overlook the timing diagrams or application notes provided in the datasheet; they offer valuable insights on how to effectively integrate the component into your design.
Remember to cross-reference any information with other sources if needed for a comprehensive understanding of how best to utilize this component in your project.
Troubleshooting Common Issues with the G5335QT2U
Having trouble with your G5335QT2U? Don’t worry, common issues can be easily resolved with some troubleshooting tips.
Ensure all connections are secure and correctly fitted. Loose connections can lead to functionality issues. Double-check the wiring diagram in the datasheet for accuracy.
If you’re experiencing signal distortion or interference, check for nearby sources of electromagnetic interference. Keep the device away from other electronic equipment.
In case of power fluctuations or irregularities, verify that the power source meets the required specifications outlined in the datasheet. Consider using a stabilizer if needed.
For any unexpected behavior or malfunctions, refer to the troubleshooting section of the datasheet for specific guidance on diagnosing and resolving issues efficiently.
Practical Applications of the G5335QT2U in Various Projects
The G5335QT2U is a versatile component that finds practical applications in various projects across different industries. In the field of electronics, this device is commonly used in circuit design for communication systems due to its reliable performance and compatibility with other components.
In robotics, the G5335QT2U plays a crucial role in motor control units, enabling precise movement and synchronization of robotic arms or vehicles. Additionally, within the automotive sector, this component is utilized in vehicle safety systems such as airbag deployment mechanisms.
Moreover, in renewable energy projects like solar panel installations, the G5335QT2U aids in monitoring and regulating power output efficiently. Its flexibility also makes it suitable for use in home automation setups for controlling lighting, heating, and security systems seamlessly.
The versatility and reliability of the G5335QT2U make it an invaluable asset across a wide range of practical applications.
Tips for Maximizing Efficiency and Performance with the G5335QT2U
When working with the G5335QT2U, there are several tips to enhance its efficiency and performance in your projects. Make sure to thoroughly study the datasheet PDF to understand all the specifications and capabilities of the component. This will help you utilize its full potential.
Additionally, consider optimizing power supply connections and signal routing for better performance. Proper grounding techniques can also significantly impact the functionality of the G5335QT2U.
Furthermore, pay attention to temperature management as overheating can affect the stability of the component. Adequate cooling solutions or thermal design considerations can prevent this issue.
Regular maintenance and updates on firmware or software related to G5335QT2U can ensure that it operates at peak efficiency over time. By implementing these tips, you can maximize the efficiency and performance of this component in your projects effectively.
Conclusion
The G5335QT2U datasheet PDF is a valuable resource for anyone working on projects that involve this component. By understanding the components and specifications, interpreting the data effectively, troubleshooting common issues, exploring practical applications, and implementing tips for maximizing efficiency and performance, you can make the most out of using the G5335QT2U in your projects. Remember to refer back to the datasheet whenever needed to ensure smooth progress and successful outcomes in your endeavors. Happy creating!

Internet
The Future of AI Writing: A Closer Look at GPT66x

Welcome to the future of writing! In a world where technology continues to push boundaries, artificial intelligence is revolutionizing the way we approach content creation. One of the most groundbreaking advancements in this field is GPT66x – a powerful tool that is changing the landscape of AI writing as we know it. Let’s delve into what makes GPT-66x so remarkable and explore its potential impact on industries reliant on written content.
What is GPT-3?
Have you ever wondered how AI is transforming the way we write? Enter GPT-3, which stands for Generative Pre-trained Transformer 3. This cutting-edge language model developed by OpenAI has been making waves in the tech world.
GPT-3 is an advanced AI system that can generate human-like text based on a given input. It uses deep learning techniques to analyze and understand the context of the text it’s fed, allowing it to produce coherent and contextually relevant responses.
With its impressive ability to mimic human writing styles and generate content across a wide range of topics, GPT-3 has revolutionized various industries, from marketing and customer service to content creation and even coding.
This powerful tool has sparked excitement among developers, writers, and businesses alike as they explore its potential applications in enhancing productivity and creativity in their respective fields.
The Advancements of GPT66x
The advancements of GPT66x mark a significant leap in the world of AI writing. This new model builds upon the foundation laid by its predecessor, GPT-3, and takes it to the next level.
GPT-66x boasts enhanced capabilities in generating human-like text, with improved accuracy and coherence. Its ability to understand context and produce more nuanced responses sets it apart from previous models.
One notable advancement is its increased understanding of specific industries and topics, allowing for more tailored content generation. This opens up possibilities for personalized writing solutions across various sectors.
Moreover, GPT-66x showcases improved language nuances and can mimic different writing styles with remarkable accuracy. Writers can leverage this technology to streamline their content creation process while maintaining authenticity.
With these advancements, GPT66x is poised to revolutionize the way we approach writing tasks in diverse fields, offering endless possibilities for creativity and efficiency.
How Does GPt66x Work?
GPT-66x operates on an intricate network of neural pathways, designed to mimic the complexities of human cognition. It processes vast amounts of data, learning patterns and structures from text inputs. By analyzing context and relationships within sentences, GPT66x generates coherent responses that emulate human-written content.
Using a combination of algorithms like transformers and attention mechanisms, GPT-66x predicts the most probable next word based on the preceding text. This predictive modeling enables it to produce flowing and contextually relevant passages.
With its massive training dataset encompassing diverse sources, GPT66x refines its language generation capabilities through continuous exposure to various writing styles and genres. As a result, it adapts to different contexts seamlessly, making it a versatile tool for content creation across industries.
The model’s ability to generate natural-sounding text has revolutionized AI writing by significantly enhancing automation in generating creative content with minimal human intervention.
The Potential Impact on Writing Industries
The potential impact of GPT-66x on writing industries is vast and transformative. With its advanced capabilities, this AI model has the power to revolutionize content creation processes across various sectors. By offering efficient and high-quality automated writing solutions, GPT-66x can streamline workflows for copywriters, marketers, journalists, and more.
One significant effect could be an increase in productivity as writers can leverage the AI’s assistance to generate initial drafts or brainstorm ideas quickly. This efficiency may lead to a higher output within shorter timeframes while maintaining quality standards.
Additionally, GPT-66x’s ability to mimic human-like language and tone opens up possibilities for personalized content creation at scale. Brands seeking tailored messaging for their target audiences can benefit from this technology by creating engaging and relevant content effortlessly.
The integration of GPT-66x into writing industries has the potential to reshape traditional practices, enhancing creativity and effectiveness in communication strategies.
Potential Concerns and Limitations
As with any technological advancement, there are potential concerns and limitations associated with the use of GPT-66x in writing. One major concern is the issue of ethical responsibility when it comes to generated content. As AI becomes more sophisticated, there may be challenges in distinguishing between human-generated and AI-generated work.
Another limitation is the risk of over-reliance on AI for content creation. While GPT-66x can assist writers by providing suggestions and ideas, there is a risk that creativity and originality could be compromised if writers become too dependent on AI tools.
Additionally, privacy and security concerns arise as GPT-66x requires large amounts of data to train effectively. There may be risks associated with storing sensitive information used for training models.
It is also important to consider biases that may exist within the dataset used to train AI models like GPT-66x, which could result in biased or inaccurate outputs. Constant monitoring and evaluation will be crucial to address these issues moving forward.
Future Developments and Possibilities
As we look to the future of AI writing, the possibilities seem endless. With advancements like GPT-66x, we can expect even more sophisticated and nuanced language generation. This could revolutionize content creation across industries, from marketing to journalism.
Imagine a world where AI can not only write articles but also craft compelling storytelling or poetry that resonates with readers on a deep emotional level. The potential for creativity and innovation in writing is truly exciting.
Furthermore, as GPT-66x continues to evolve, it may become increasingly adept at understanding context and tone, making its output even more tailored to specific audiences. This could lead to highly personalized and engaging content that captivates readers effortlessly.
The integration of AI writing tools into everyday workflows might streamline processes and boost productivity for writers, allowing them to focus more on ideation rather than mundane tasks like grammar checking or fact verification.
In essence, the future developments in AI writing hold immense promise for transforming how we create and consume content in ways we have yet to fully grasp.
Conclusion
The future of AI writing is rapidly evolving with the advancements made by models like GPT66x. As technology continues to progress, we are likely to see even more sophisticated AI systems that can mimic human writing with unprecedented accuracy.
While there are concerns about potential misuse and ethical implications, the possibilities for enhancing creativity, efficiency, and accessibility in writing industries are immense. With proper oversight and guidance, GPT-66x and its successors have the potential to revolutionize how we approach content creation.
As we embrace the era of AI-assisted writing tools like GPT-66x, it’s essential to understand both their capabilities and limitations. By leveraging these technologies responsibly, we can harness their power to unlock new opportunities and redefine the way we interact with language in the digital age.
Internet
Wadware: The Silent Threat Lurking in Cyberspace

Welcome to the shadowy realm of cyberspace, where unseen threats lurk in the digital shadows. Among these silent menaces lies a cunning adversary known as Wadware – a stealthy form of malware that can wreak havoc on individuals and businesses alike. In this blog post, we will delve into the world of Wadware, exploring its various types, impacts, and, most importantly, how you can safeguard yourself against its insidious attacks. So buckle up and get ready to navigate the treacherous waters of cybersecurity with us!
Types of Wadware and How They Work
Wadware comes in various forms, each designed to infiltrate systems and wreak havoc. One common type is adware, which bombards users with unwanted advertisements by tracking their online activities. Spyware is another insidious variant that stealthily monitors user behavior, collecting sensitive information without consent.
Keyloggers are a particularly malicious form of wadware that record keystrokes and login credentials, posing a significant threat to personal privacy and security. Another type is ransomware, which encrypts files or locks users out of their devices until a ransom is paid.
Moreover, Trojans disguise themselves as legitimate software to deceive users into downloading them, allowing cybercriminals access to the victim’s system. Rootkits are yet another dangerous form of wadware that can hide deep within the operating system, making detection and removal challenging for even seasoned cybersecurity professionals.
The Impact of Wadware on Individuals and Businesses
Wadware poses a significant threat to both individuals and businesses in the digital realm. For individuals, falling victim to wadware can result in compromised personal information, financial loss, and even identity theft. The invasion of privacy that comes with wadware attacks can be distressing and have long-lasting consequences on one’s sense of security.
On the other hand, for businesses, the impact of wadware can be catastrophic. From confidential data breaches to operational disruptions, wadware attacks can lead to substantial financial losses and damage to reputation. The costs associated with mitigating these attacks and rebuilding trust with customers can be overwhelming for businesses of any size.
In today’s interconnected world, where data is increasingly valuable, safeguarding against wadware is crucial for both individuals and organizations alike. Vigilance in detecting potential threats and implementing robust cybersecurity measures are essential in combating this silent but pervasive danger lurking in cyberspace.
How to Protect Yourself from Wadware Attacks
In the ever-evolving landscape of cybersecurity, protecting yourself from wadware attacks is crucial. Start by ensuring your devices have up-to-date antivirus software and firewalls. Regularly update your operating systems and applications to patch vulnerabilities that wadware can exploit.
Be cautious when clicking on links or downloading attachments from unknown sources, as they could be vehicles for wadware infiltration. Avoid visiting suspicious websites and always verify the legitimacy of emails before interacting with them.
Implement strong passwords and enable two-factor authentication whenever possible to add an extra layer of security. Backup your important data regularly to prevent loss in case of a wadware attack.
Stay informed about the latest cybersecurity threats and trends to stay one step ahead of potential wadware attacks. Remember, vigilance is key when it comes to safeguarding your digital assets from malicious actors lurking in cyberspace.
Case Studies: Real-Life Examples of Wadware Attacks
Imagine a scenario where a small business owner wakes up one morning to find their entire customer database compromised by Wadware. Personal information, credit card details, and sensitive data stolen in the blink of an eye. The aftermath? A reputation tarnished, trust shattered, and financial losses that could cripple the business.
In another case, a cybersecurity firm fell victim to a sophisticated Wad-ware attack targeting their research and development files. Months of hard work and innovation gone in an instant as hackers encrypted crucial data for ransom.
These real-life examples serve as stark reminders of the devastating impact wadware attacks can have on individuals and businesses alike. It’s not just about losing data; it’s about losing trust, credibility, and potentially everything you’ve worked so hard to build. Stay vigilant, stay informed – because in today’s digital landscape, no one is immune to the silent threat of wadware lurking in cyberspace.
The Future of Wadware and Cybersecurity Measures
As technology continues to advance, the future of wadware poses an ongoing threat in cyberspace. With cybercriminals constantly evolving their tactics, it is crucial for individuals and businesses to stay vigilant.
Cybersecurity measures are also adapting to combat these sophisticated attacks. From advanced encryption protocols to robust firewalls, organizations are investing heavily in protecting their digital assets.
Machine learning and artificial intelligence are being integrated into cybersecurity systems to detect and prevent wadware attacks more effectively. By analyzing patterns and anomalies in data traffic, these technologies can proactively defend against threats.
Additionally, cloud-based security solutions offer scalability and flexibility in safeguarding networks from wadware infiltration. As more data migrates to the cloud, ensuring its protection becomes paramount.
Collaboration among industry experts, government agencies, and cybersecurity professionals will be essential in staying ahead of wadware developments. The collective effort towards sharing threat intelligence and best practices will strengthen our defense mechanisms against future cyber threats.
Conclusion
As technology continues to advance, so do the threats in cyberspace. Wadware poses a silent but dangerous risk to individuals and businesses alike. With its ability to evade detection and cause significant harm, it is crucial for everyone to be aware of this threat and take proactive measures to protect themselves.
By understanding the types of wadware attacks and how they work, individuals can better safeguard their devices and personal information. Implementing cybersecurity best practices such as regularly updating software, using strong passwords, and being cautious of suspicious links or downloads can help mitigate the risks associated with wad-ware.
Furthermore, organizations must invest in robust cybersecurity measures to defend against sophisticated wad-ware attacks that could potentially compromise sensitive data and disrupt business operations. Regular security assessments, employee training programs, and implementing multi-layered defense mechanisms are essential steps in fortifying defenses against evolving cyber threats like wad-ware.
In a constantly evolving digital landscape, staying informed about emerging threats like wad-ware is crucial for maintaining a secure online presence. By taking proactive steps to enhance cybersecurity resilience at both individual and organizational levels, we can collectively combat the silent threat lurking in cyberspace – wad–ware.
Internet
Understanding the Role of Certidor in Ensuring Data Security and Integrity

In a world where data is the new gold, safeguarding its security and integrity has become paramount. Welcome to the realm of Certidor, your guardian angel in the digital space. Let’s dive into how Certidor plays a vital role in ensuring that your data remains safe from prying eyes and tampering hands.
The Importance of Data Security and Integrity
In today’s digital age, data security and integrity are paramount for businesses and individuals alike. With the increasing frequency of cyber threats and data breaches, safeguarding sensitive information has never been more critical.
Data security ensures that confidential data remains protected from unauthorized access or malicious attacks. It involves implementing robust measures to prevent data leaks, theft, or manipulation.
Maintaining data integrity is equally important as it ensures that information remains accurate, consistent, and reliable. Any compromise in data integrity can lead to misinformation, financial losses, or reputational damage.
By prioritizing data security and integrity, organizations can build trust with their customers by demonstrating a commitment to protecting their personal information. This not only enhances brand reputation but also helps avoid costly legal consequences associated with data breaches.
Investing in robust data security measures is essential for safeguarding valuable assets and maintaining trust in an increasingly interconnected world.
How Certidor Works
Certidor operates as a sophisticated platform designed to ensure the security and integrity of data. Its working mechanism involves employing advanced encryption
techniques to safeguard sensitive information from unauthorized access. By utilizing cutting-edge technology, Certidor encrypts data at rest and in transit, providing users with peace of mind regarding their confidential data.
Furthermore, Certidor implements secure authentication processes to verify the identities of individuals accessing the system. This multi-factor authentication adds an extra layer of protection against potential breaches or cyber threats. Additionally, Certidor continuously monitors for any suspicious activities or anomalies within the database, promptly alerting administrators to take necessary actions if required.
In essence, Certidor’s seamless integration of encryption protocols and robust authentication measures establishes a fortified barrier around valuable data assets. Through its intricate workings, Certidor stands as a reliable guardian ensuring that critical information remains shielded from malicious intent.
Benefits of Using Certidor for Data Protection
When it comes to data protection, Certidor offers a range of benefits that make it a valuable tool for businesses and individuals alike. One key advantage is the ability to ensure the integrity of your data through secure blockchain technology. By storing data in an immutable ledger, Certidor provides a tamper-proof way to verify the authenticity of information.
Additionally, using Certi-dor can enhance trust and transparency with clients and partners by demonstrating a commitment to safeguarding sensitive data. This not only helps build credibility but also strengthens relationships based on mutual trust.
Moreover, Certi-dor streamlines the process of verifying documents and information, saving time and reducing manual errors. This efficiency boost can lead to cost savings and improved productivity for organizations looking to optimize their data management processes.
Leveraging Certidor for data protection can bring peace of mind knowing that your information is secure, trustworthy, and easily verifiable—a crucial aspect in today’s digital landscape where privacy and security are paramount concerns.
Real-Life Examples of Successful Data Protection with Certidor
In real-life scenarios, Certidor has played a crucial role in safeguarding sensitive data for businesses of all sizes.
One company, a leading financial institution, utilized Certidor to ensure the security and integrity of their clients’ financial information. By implementing Certidor’s innovative technology, they were able to prevent unauthorized access and potential breaches effectively.
Another example comes from a healthcare organization that leveraged Certidor to protect patient records and comply with stringent privacy regulations. With Certidor’s robust encryption methods in place, they successfully maintained the confidentiality of patient data while improving overall operational efficiency.
Moreover, an e-commerce retailer integrated Certidor into their systems to secure customer payment details during online transactions. This proactive approach not only boosted consumer trust but also shielded the company from cyber threats.
These success stories underscore how Certidor empowers businesses across diverse industries to fortify their data defenses and uphold trust with stakeholders.
The Future of Data Security with Certidor
As technology continues to advance at a rapid pace, the future of data security is more crucial than ever. Certidor is at the forefront of this evolution, offering innovative solutions to protect sensitive information from cyber threats.
With increasing numbers of data breaches and hacks occurring globally, businesses and individuals are seeking robust measures to safeguard their digital assets. Certidor’s cutting-edge encryption techniques and secure authentication processes are paving the way for a more secure online environment.
In the coming years, we can expect Certidor to further enhance its capabilities, staying ahead of emerging cybersecurity challenges. By leveraging artificial intelligence and machine learning technologies, Certidor is poised to offer even more advanced protection against evolving cyber threats.
The partnership between technology and cybersecurity will continue to shape how we safeguard our data in an increasingly interconnected world. As organizations strive to stay one step ahead of hackers, Certidor remains a trusted ally in ensuring data security for years to come.
Conclusion
In a digital landscape where data security and integrity are paramount, Certidor emerges as a reliable ally in safeguarding sensitive information. By providing robust mechanisms for verification and validation, Certidor plays a crucial role in ensuring that data remains secure and unaltered.
As technology continues to advance and cyber threats evolve, the need for trusted solutions like Certidor will only grow. Organizations across various industries can benefit from incorporating Certidor into their data protection strategies to mitigate risks and uphold the trust of their stakeholders.
With its innovative approach to verifying the authenticity of data, Certi-dor is poised to shape the future of data security. By leveraging blockchain technology and cryptographic techniques, Certidor offers a secure foundation for maintaining the integrity of digital assets.
As we look ahead to an increasingly interconnected world, embracing tools like Certidor will be key to establishing a more secure digital ecosystem. With its proven track record and forward-thinking approach, Certi-dor stands out as a valuable asset in safeguarding against data breaches and ensuring trust in online transactions.
Incorporating Certi-dor into your organization’s cybersecurity framework is not just about compliance; it’s about instilling confidence in your customers and partners that their data is protected. Embrace the power of Certidor today and fortify your defenses against evolving cyber threats.
-

 Business2 months ago
Business2 months agoWhat does Incumbent mean in business?
-

 Text2 months ago
Text2 months agoPH
-

 Text2 months ago
Text2 months agoWhat does smh mean in text?
-

 Text2 months ago
Text2 months agoKN
-

 News1 month ago
News1 month agoDiscover MyLawyer360: Your One-Stop Legal Assistance Hub
-

 Business1 month ago
Business1 month agoLessInvest.com Crypto: Your Gateway to Smarter Investments
-

 sports1 month ago
sports1 month agoThe Versatile Talent of ben foster: A Deep Dive into His Career
-

 Health1 month ago
Health1 month agoThe Comprehensive Guide to Mega-Personal.net Health Archives